A Better Implementation of SecureString Passwords for Powershell Modules
Function Test-Function{
[CmdletBinding(DefaultParameterSetName='None')]
param(
[Parameter(Mandatory=$True, Position=1, ParameterSetName='Peer')]
[ArgumentCompleter({
param ( $commandName,
$parameterName,
$wordToComplete,
$commandAst,
$fakeBoundParameters )
if([string]::IsNullOrEmpty($fakeBoundParameters.PassPhrase)){
$Script:PassPhrase = ([System.Management.Automation.PSCredential]::new(' ', $(Read-Host -AsSecureString))).GetNetworkCredential().Password
$count = '~' * ($PassPhrase.length / 2 )
$Script:ReturnableValue = "$($count + "SECUREPASSWORD" + $count)"
return $Script:ReturnableValue
}
})]
[String]$PassPhrase = $Script:ReturnableValue,
[parameter(DontShow)]
$VerbosePreference,
[parameter(DontShow)]
$WarningPreference,
[parameter(DontShow)]
$ConfirmPreference,
[parameter(DontShow)]
$DebugPreference
)
if($PassPhrase -notmatch $Script:ReturnableValue){
Write-Warning 'SecureString form of password is mandatory. Please use tab-completor with the parameter and try again.'
break;
}
}
As I started learning how to use Register-ArgumentCompletor as well as dynamic parameters back in the day, I was always curious about if passwords could be efficiently and securely integrated using them. So, I started researching and basically going into a rabbit hole of searching forums, including Reddit, where I asked many times if this could be done, but could not find a solid answer. It was the usual "Its not possible" or "The only way is to use Read-Host [-AsSecureString] and specify it after the module or script executes". Eventually I gave up and time moved on and I started having a better understaing of Powershell. I then got into making modules, one of which led me back to this rabbit hole. One of the parameters of the module is for a password and well... here we go again. But as I researched more this time, I stumbled across a guide on whats called ArgumentCompletor, which is similar to Register-ArgumentCompletor, but allows me to encapsulate the functionality into my code instead of making it external to the code itself. More great info can be found by > Dr. Tobias Weltner <. With the information found there, I started messing around with stuff and started stumbling onto what eventually became a successful implentation.
Lets get started!
To save some time, I have created the structure already and as a side note, for this took work we must
{TAB} TO ACTIVATE AND {ENTER} TO LEAVE THE ARGUMENTCOMPLETOR.
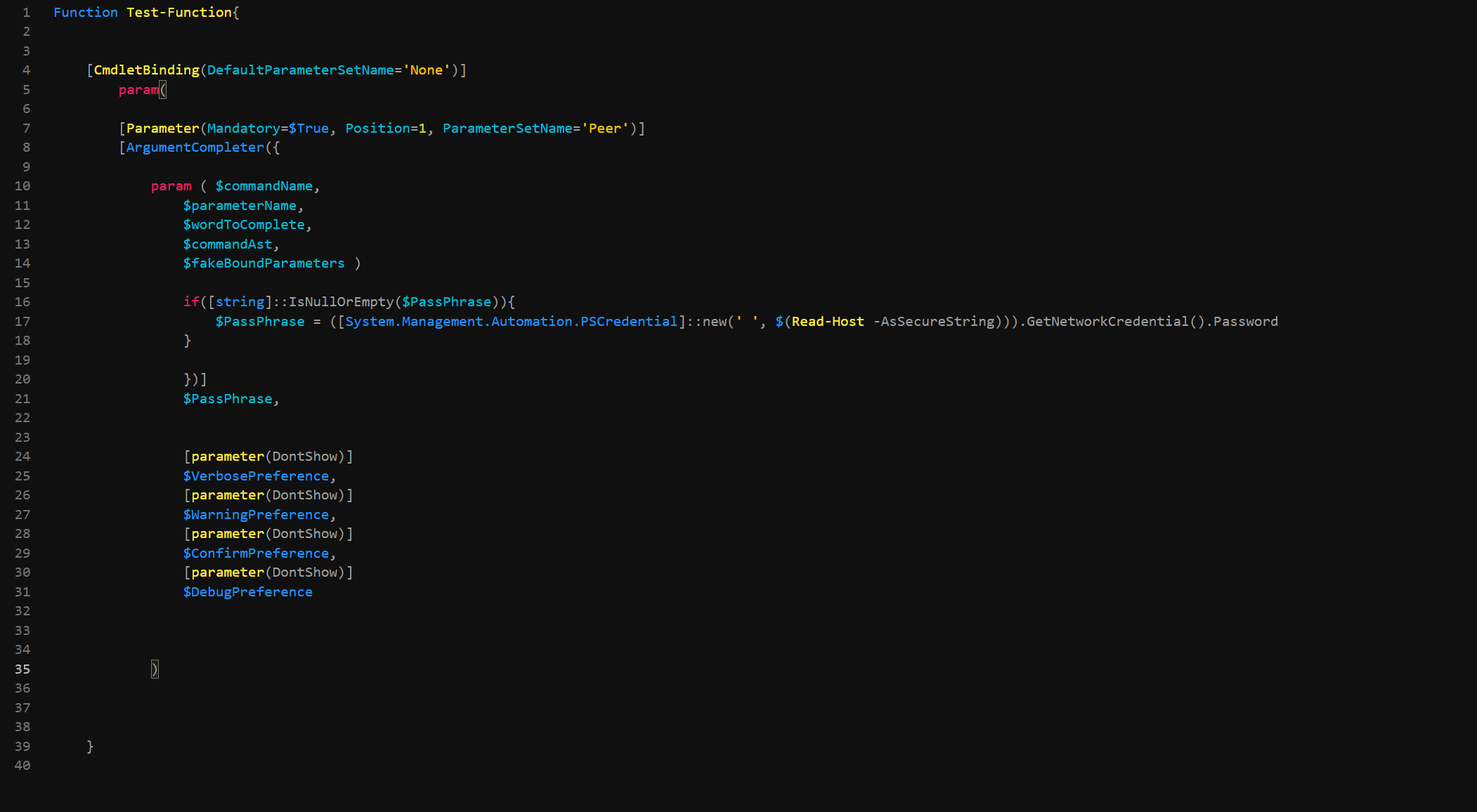

if([string]::IsNullOrEmpty($PassPhrase)){}
we can see that the parameter itself is being passed into the argument. This is wrong because the parameter itself does not have a value contained until AFTER the module has started running. So what actually needs to happen is we need to make use of what is known as $fakeBoundParameters. These are initialized inside of the argument container and can hold a value as the argument is executed. So, with this new bound, lets try the code again and see what the result is...
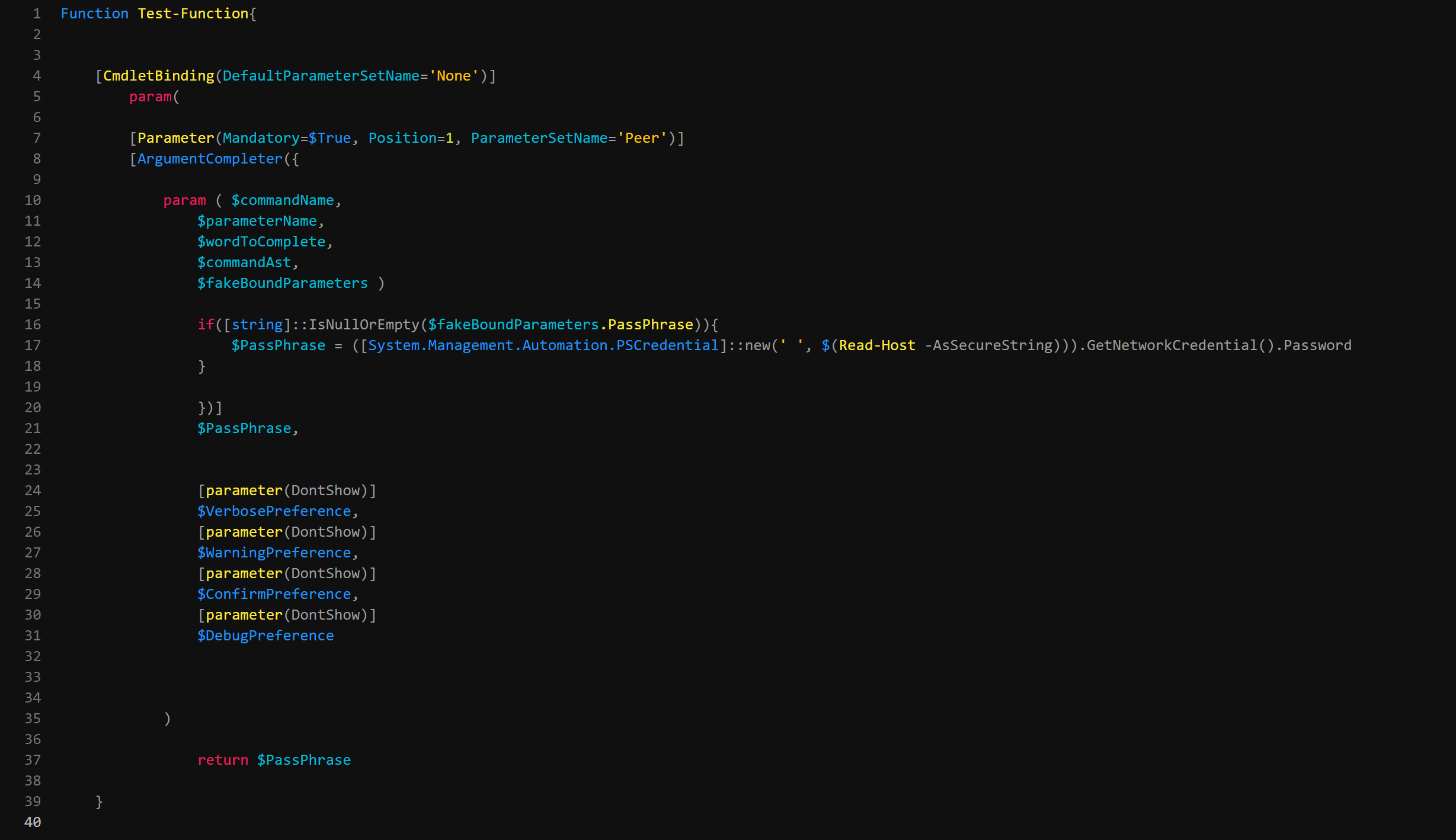


Well, this is because the container that we passed the code into $SomeArbitraryVar is only able to be utilized within that argumentcompletor codeblock. This is useful in general incase you need to hold onto data passed within it, to use with other statements used within the same container, but this isnt useful for use because we need to be able to use it outside of the ArgumentCompletor itself. So, why not use a Global scope so we can break it free from its containment? Well, we could, but Global scopes are highly frowned upon for their security risks and possibilities of breaking objects of other scripts and such. So, what we need is something that can allow us to free our variable from its immediate containment, but still stay within the confinds of the script or session its executed in. The scope we will use for this is the $Script: Scope. More information on scopes by > Tyler Muir <.
So now, lets test this...
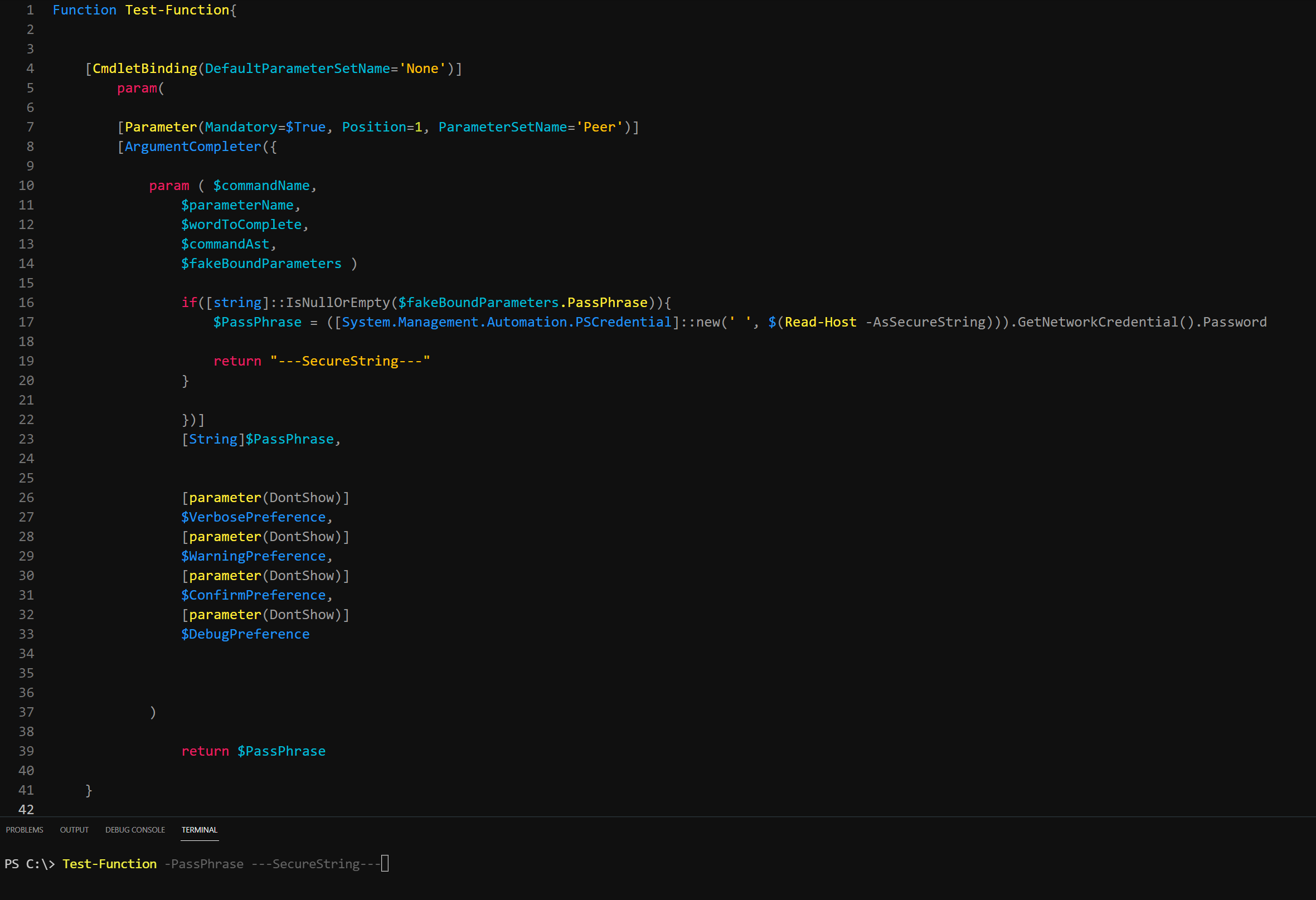
As a side note, we can actually use the parameters name itself because the regular $PassPhrase and the elevated $Script:PassPhrase are used as 2 separate containers for our code.
Lets watch!
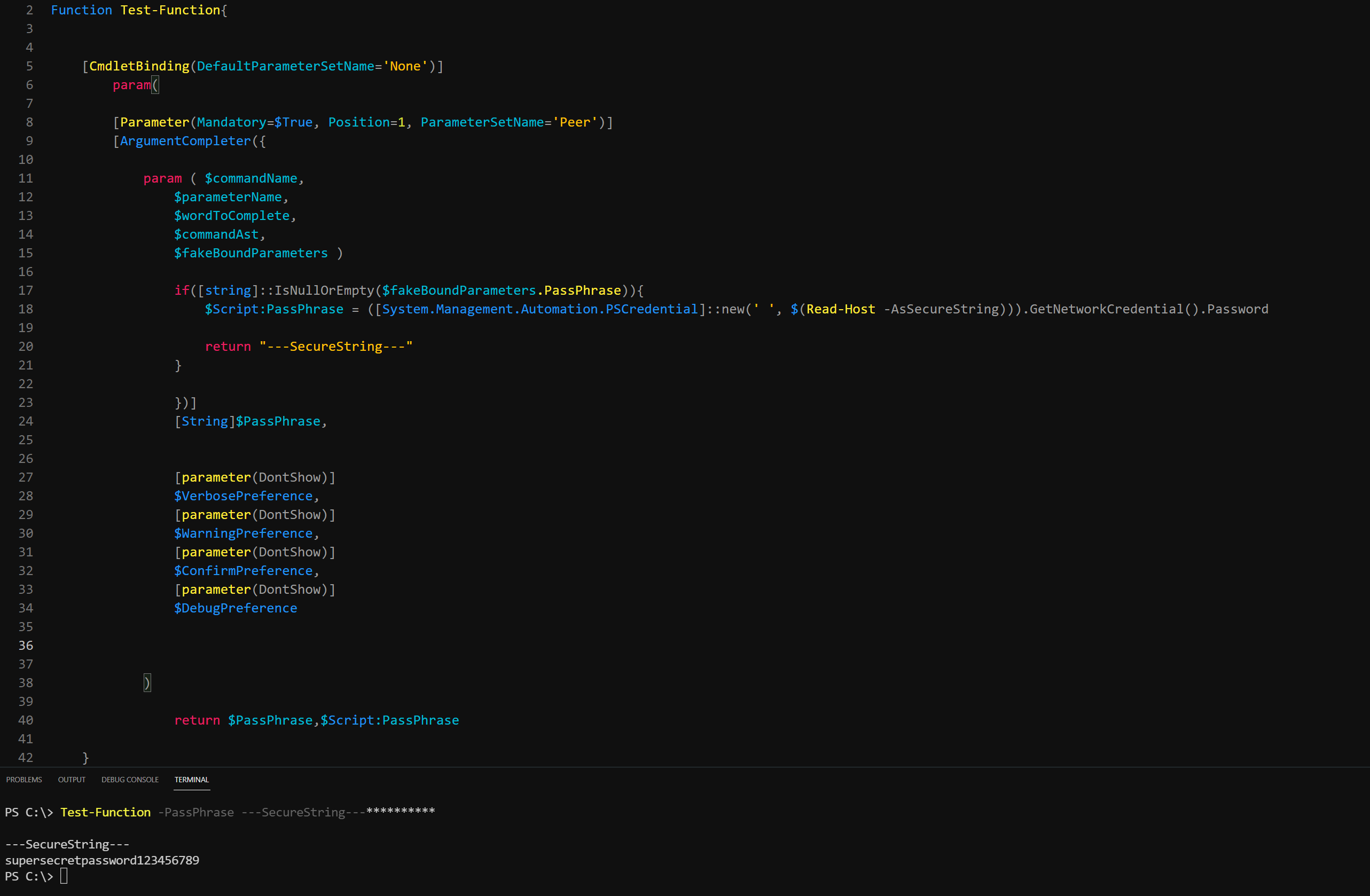
---SecureString---
value but it left additional asterisks at the end. This leads me to believe that when the value is returned, the console cannot clear itself before returning the given value, resulting in something that looks like a console glitch. But this is merely due to the way the console is designed. So why not Clear-Host before returning the value? Well, because this implementation will have a glitch type effect as well. So what we need is a way to have the returned value be longer than the securestring itself. This is where we can introduce math and get a little creative.
Lets watch!
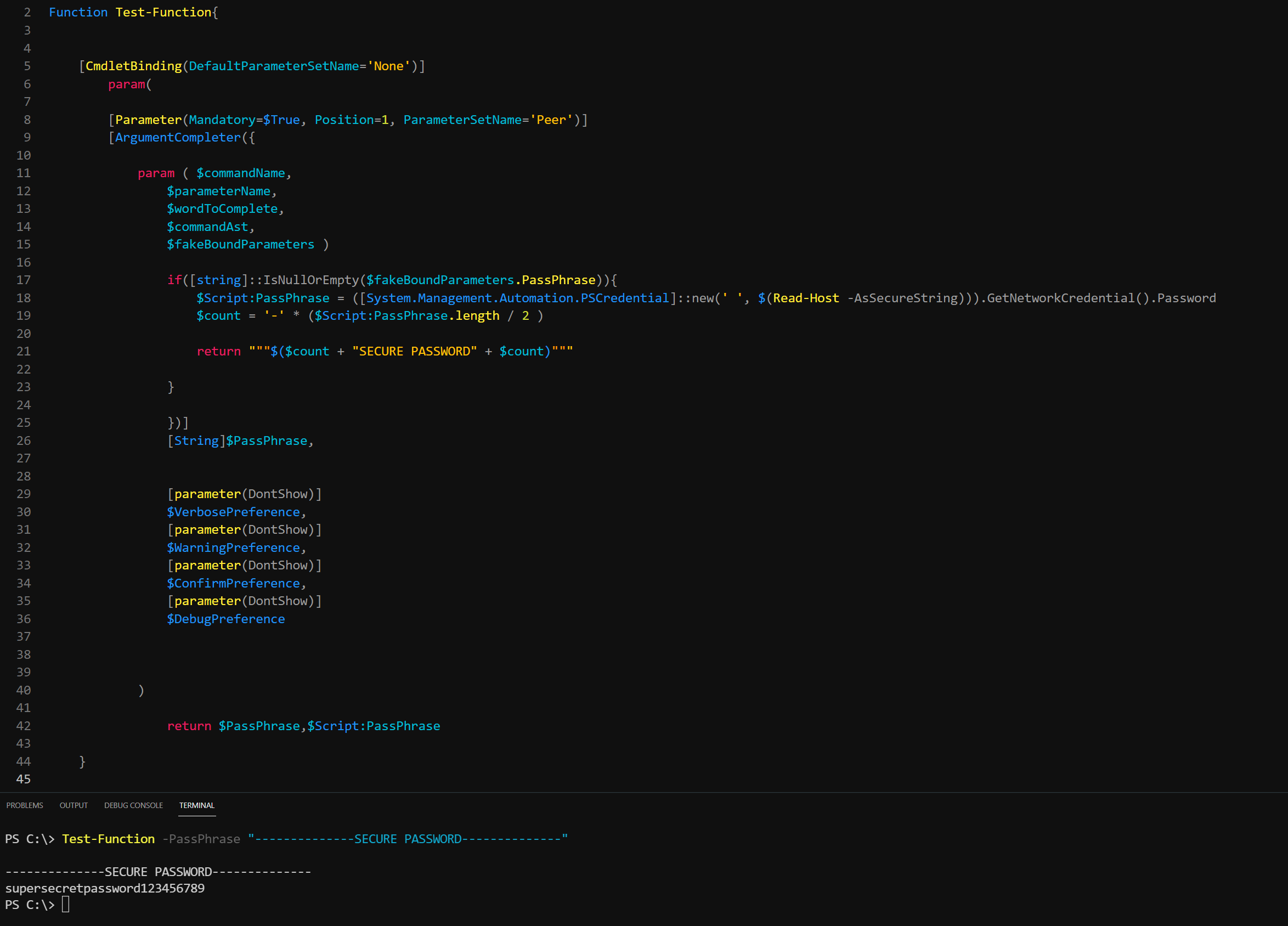
So now we have a general understanding of how to implement this. But how does it pan out in a real world example and what measures need to be in place to ensure that the module takes this implentation seriously? Lets dive a little deeper as we are not quite at the end of the journey presented in the first image of this guide.
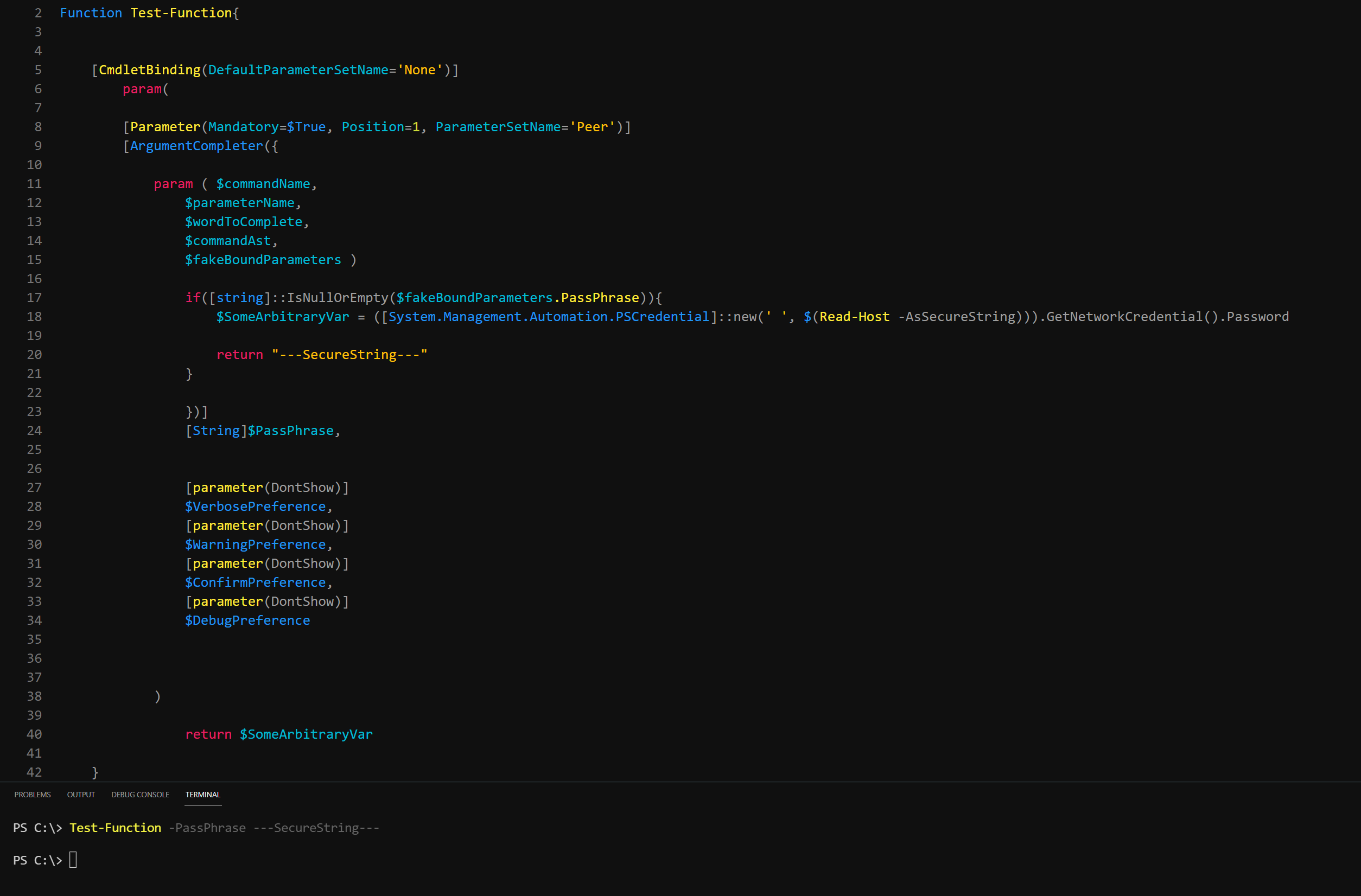
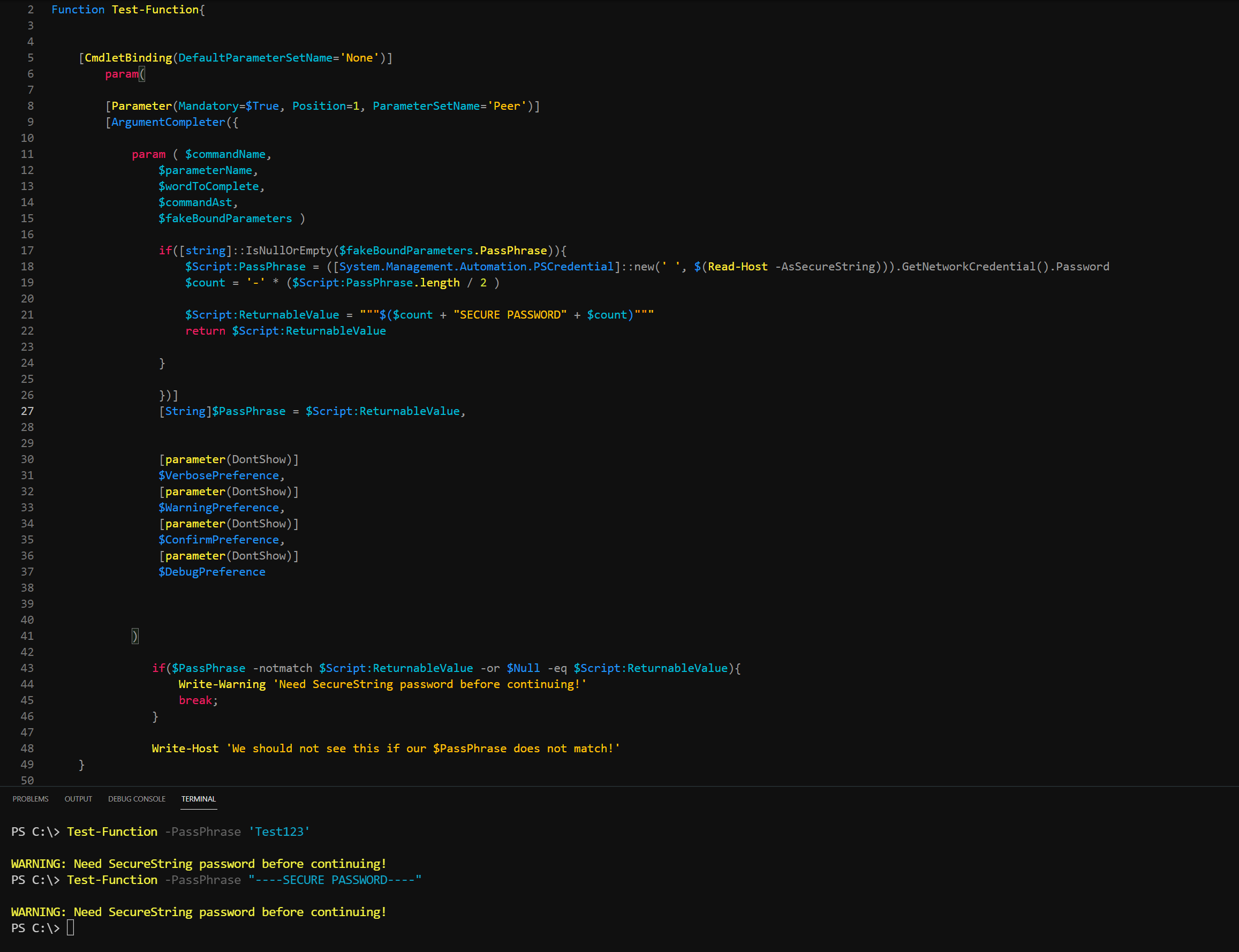
We can run the code below which is just a plain-text value as see how its presented to the console, as well as the end result compared to our elevated version of the variable.

We need to create an if statement to produce this effect. But first, we need to take the value returned to the console and place that into a variable itself so we have something to compare in the if statement. Then, we will return that value, but also add it as the default $PassPhrase value. This is to ensure that if the end user types a plain-text value, it will replace the default of our secure-string returned value, thus triggering the if statement. Incase its the first time that is ran, we will also add an -or statement with it as the elevated variable may not have a value yet.
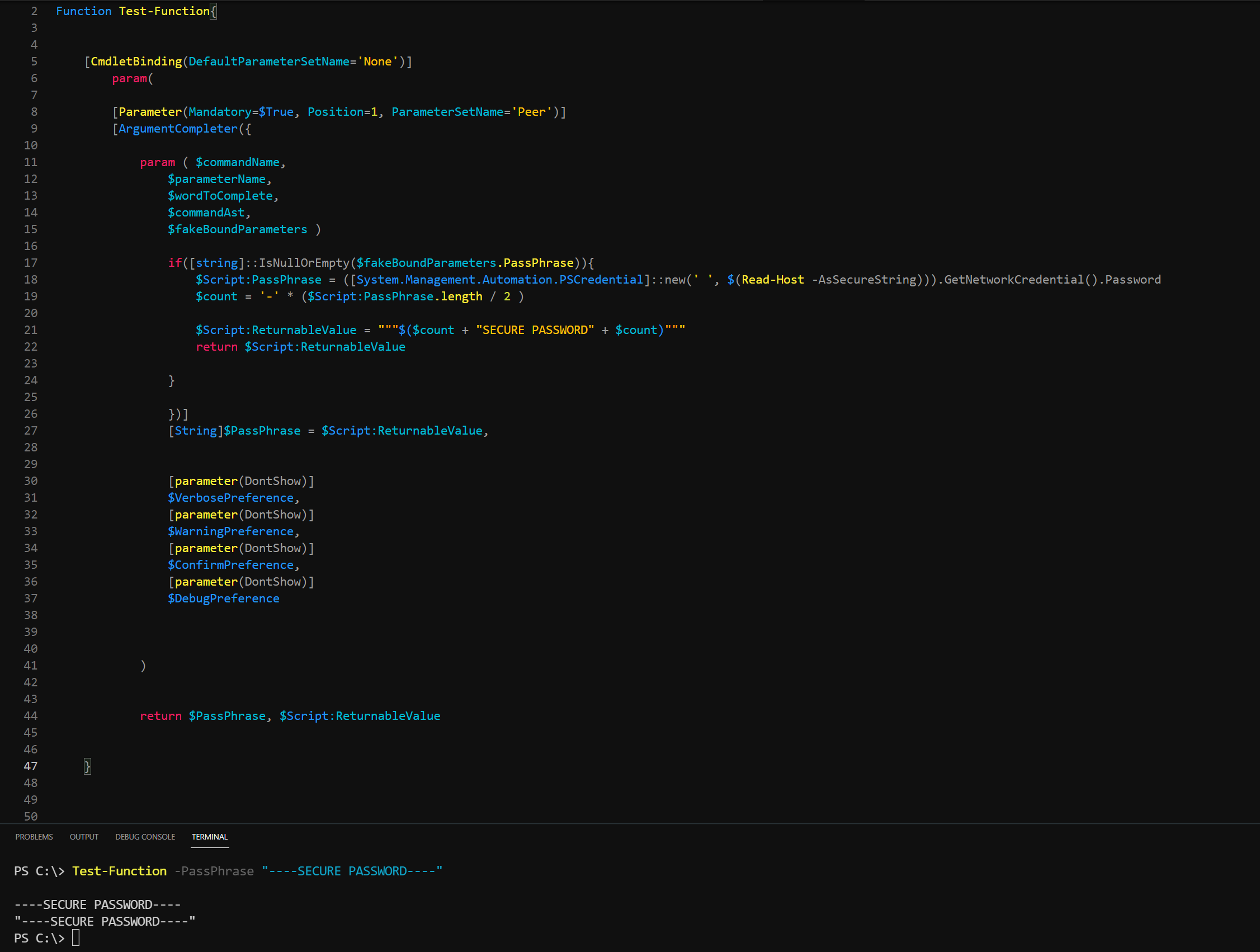
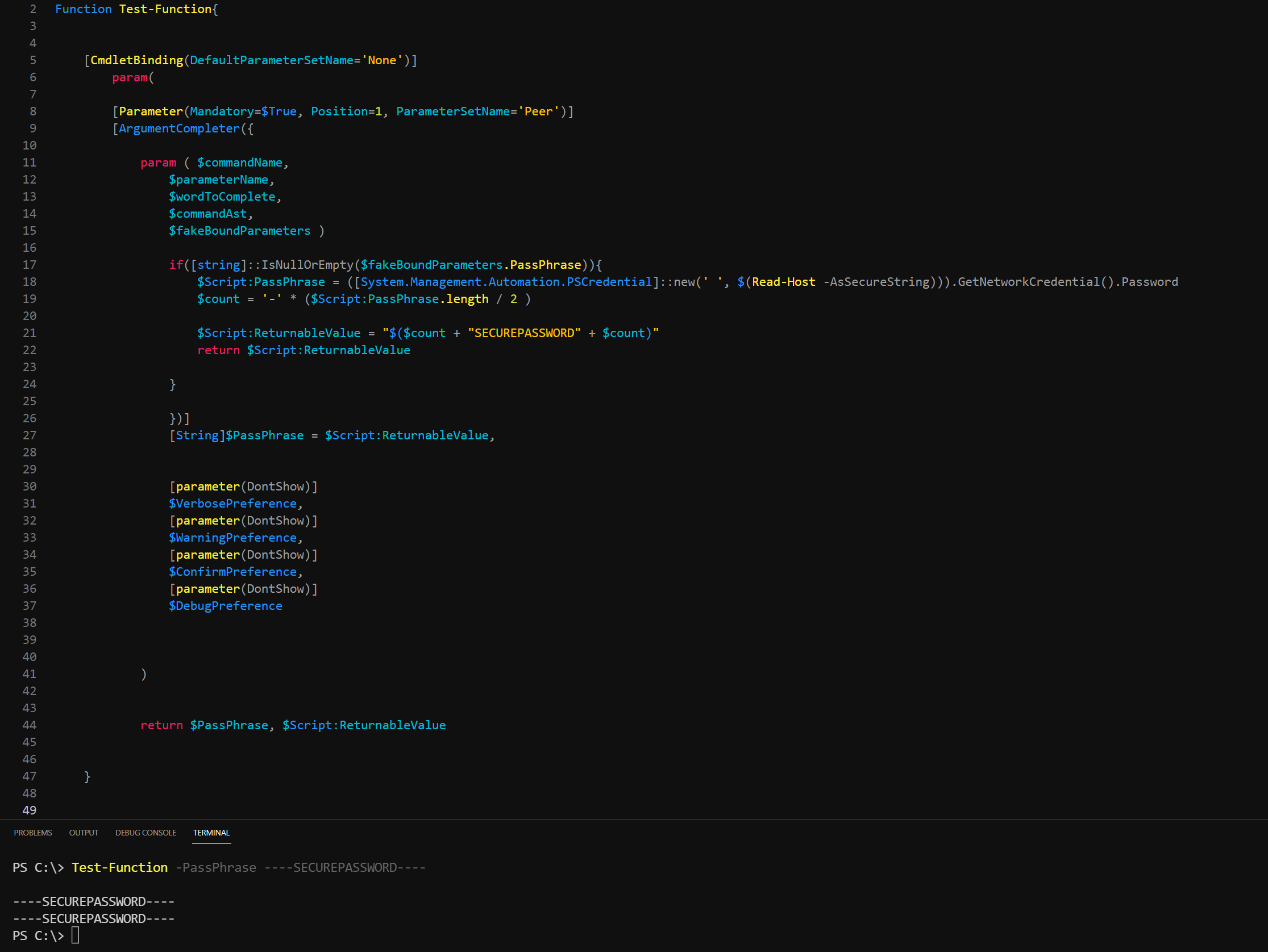
Test-Function -PassPhrase ----SECURE-PASSWORD----
----SECURE-PASSWORD---- has the same color as the -PassPhrase parameter itself. I thought this was odd so I did some testing with other symbols and oddly enough I was not surprised with the results.
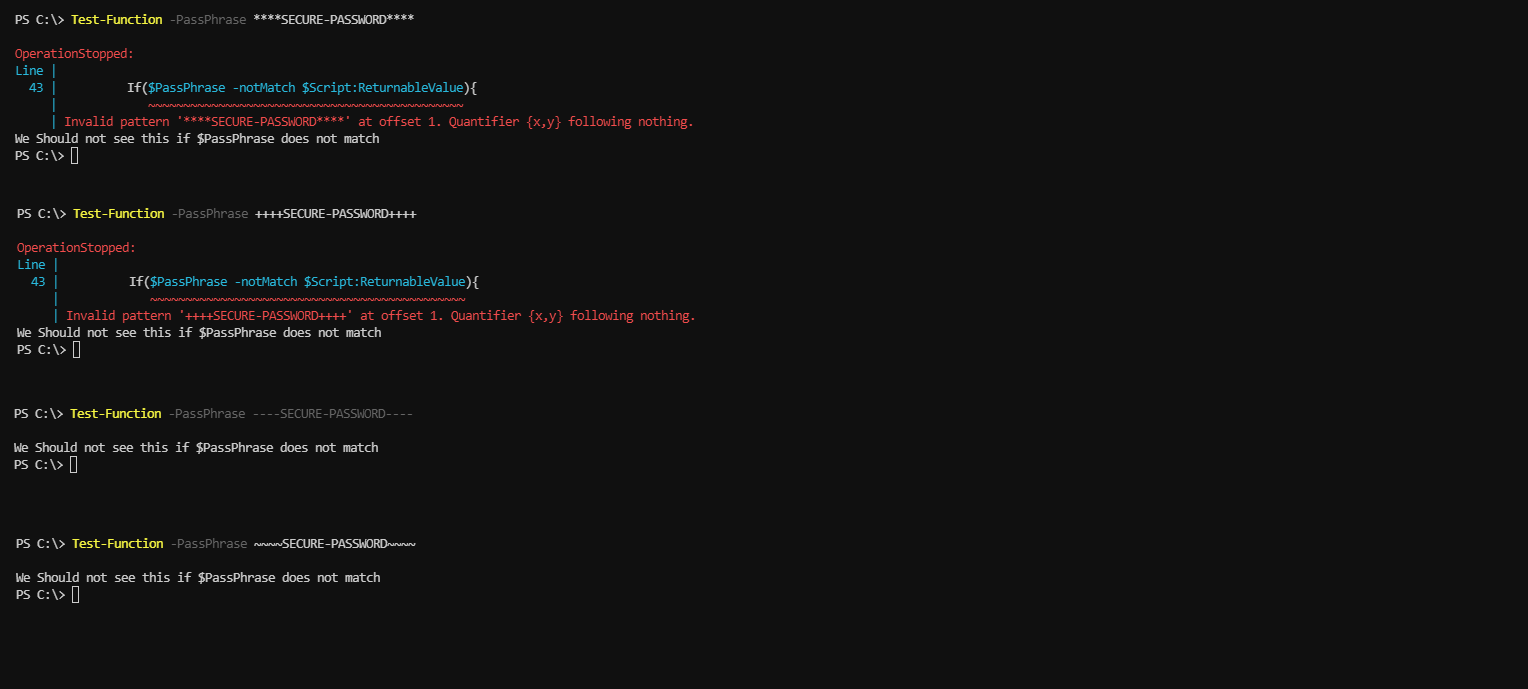
With this knowledge we are now ready to execute a live example of this implentation working properly. Ill be back once I have set this up...
Let's Test this!
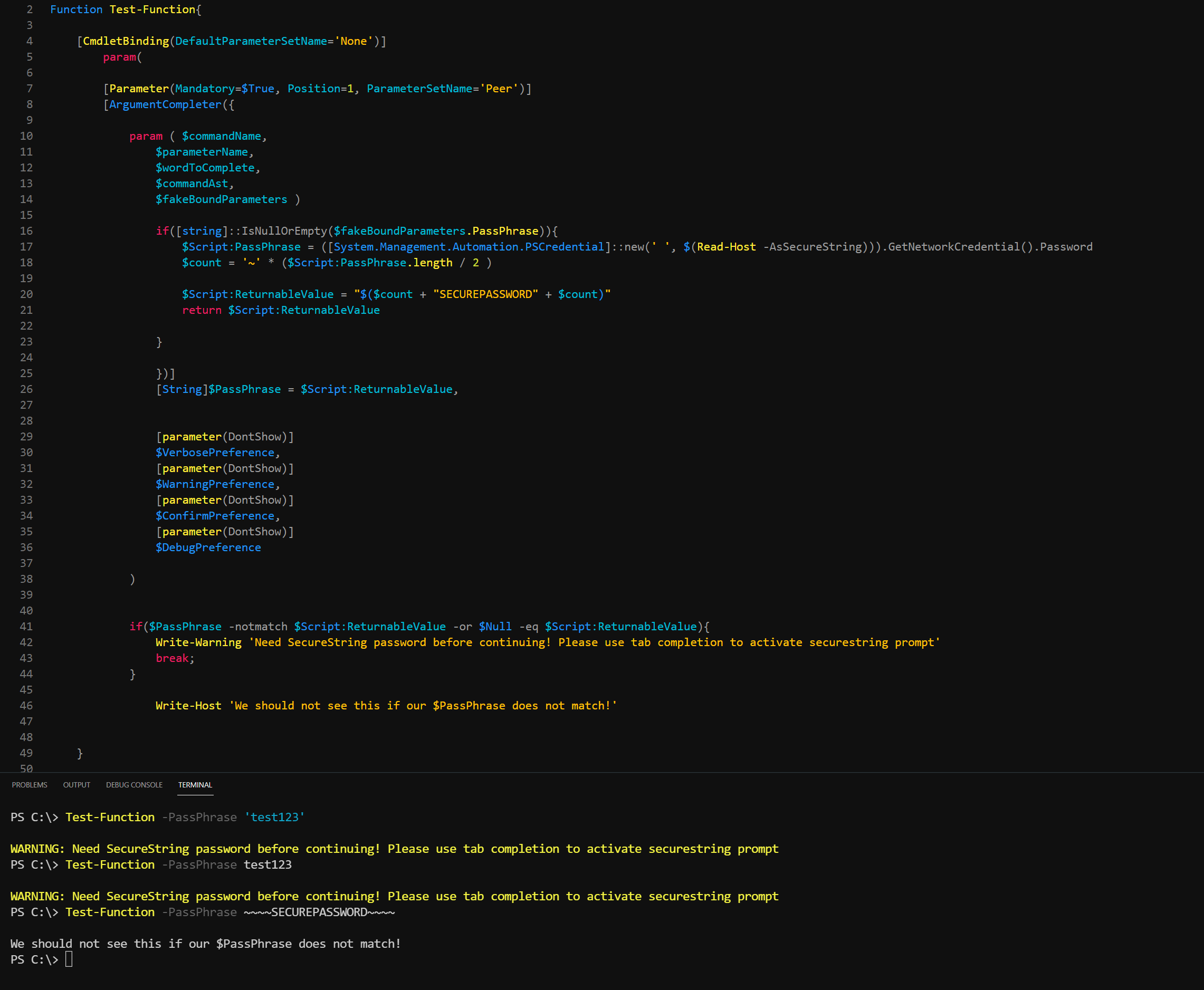
A safe and effective way to implement securestring passwords into modules and placing a security measure to ensure your module enforces its use.